A Guide to HIPAA-Compliant Application Development
Building an application that handles health data means you’re operating under a different set of rules. We’re talking about HIPAA-compliant application development: the craft of creating software that meets the tough security and privacy standards set by the Health Insurance Portability and Accountability Act. This isn’t just about ticking boxes; it’s about engineering your application from the ground up with robust safeguards like end-to-end encryption, iron-clad access controls, and meticulous audit logging.
For any app that touches Protected Health Information (PHI), this isn’t optional. It’s the absolute baseline.
Why HIPAA Compliance Is a Business Imperative
In today’s healthcare landscape, HIPAA compliance has evolved from a legal chore into a powerful business strategy. Gaining and keeping the trust of users is everything, and that trust is built on a foundation of uncompromising data security. With remote care and connected health devices becoming the norm, the pressure to build secure applications has never been higher.

Market Forces Driving the Need for Compliance
The digital health market is absolutely exploding. It’s on track to jump from $427 billion in 2025 to a staggering $1.5 trillion by 2032. This growth is fueled by software that needs to manage PHI flawlessly.
Here’s the catch: a recent study found that 68% of healthcare organizations feel their outdated and siloed software is holding them back from achieving their digital goals. This disconnect creates a massive opportunity for well-designed, compliant applications to step in and solve real problems.
Building with a “compliance-first” mindset isn’t just about avoiding fines; it’s about gaining a serious competitive advantage. As we explored in our guide to compliance-first software development, this philosophy is key to long-term success.
A strategic shift happens when you stop seeing HIPAA as a burden and start seeing it as a competitive advantage. It opens doors to new markets, builds unshakable patient trust, and sets your app up for success.
Overcoming Common Development Hurdles
So, why isn’t everyone jumping on this opportunity? Many healthcare organizations get stuck trying to innovate around some very common, very real obstacles. Trying to make new apps talk to ancient legacy systems, keeping up with dense regulations, and ensuring data can move freely but securely can stop a project dead in its tracks.
These issues often create a messy, fragmented data environment that’s both inefficient and a security nightmare. A smarter approach tackles these problems from day one, building a secure, scalable foundation for your project.
You’ll almost certainly run into these challenges:
-
Legacy System Integration: How do you connect your sleek, modern app to a clunky, old Electronic Health Record (EHR) system without opening up security holes?
-
Evolving Regulations: HIPAA isn’t static. You have to stay on top of changes to data privacy laws that directly affect how your software is designed and maintained.
-
Vendor Management: Every third-party tool, API, or service you use must also be HIPAA-compliant. This means they need to be willing to sign a Business Associate Agreement (BAA), and not all of them are.
By weaving compliance into the very fabric of your development process, you can turn these roadblocks into the core strengths of your application. This is how you build a tool that both patients and providers can rely on.
Getting to Grips with the HIPAA Security and Privacy Rules
Before your team even thinks about writing a single line of code, you have to understand the rules of the road. Building a HIPAA-compliant application isn’t a “move fast and break things” kind of project. It’s a deliberate process of engineering software that meets very specific federal standards designed to keep patient data safe.
The two big pillars you need to know are the HIPAA Privacy Rule and the Security Rule.
Think of the Privacy Rule as the “why” and “who.” It sets the national standards for who can access and use Protected Health Information (PHI). For a development team, this means your application must be built to enforce these boundaries, ensuring PHI is only used for legitimate reasons (like treatment or payment) and only by people who are explicitly authorized.
The Security Rule is where we get into the technical nuts and bolts. This is the “how.” It lays out exactly how electronic PHI (ePHI) must be protected from threats and unauthorized access. It’s organized into three types of safeguards, each one directly impacting how you’ll build your app.
The Three Safeguards of the HIPAA Security Rule
The Security Rule’s safeguards aren’t just vague suggestions; they are hard requirements that translate directly into your application’s architecture, features, and even your team’s internal processes. Getting these right from the start is non-negotiable.
Let’s quickly break down what these mean in practice.
Here’s a quick reference table to keep these straight. Think of it as a cheat sheet for translating HIPAA requirements into development tasks.
HIPAA Safeguards at a Glance
| Safeguard Type | Core Principle | Key Implementation Requirements |
|---|---|---|
| Administrative Safeguards | The "people and processes" part of security. | Running regular risk assessments, appointing a security officer, mandatory employee training, and properly managing all your vendor contracts (BAAs). |
| Physical Safeguards | Securing the actual hardware where ePHI lives. | Locking down data centers (your cloud provider helps here), controlling who can access workstations, and having clear policies for laptops and mobile devices. |
| Technical Safeguards | The technology you build and configure to protect data. | Unique user IDs for everyone, strong end-to-end encryption (both in transit and at rest), detailed audit logs, and automatic session log-offs. |
Understanding these safeguards is the first step in building a compliant architecture. They form the foundation upon which every other technical decision rests.
Turning Legalese into Actionable Dev Tasks
So, how does this all translate into actual work for developers? Let’s make it real.
When HIPAA talks about the “access control” standard, it means your backend absolutely must implement strict role-based access control (RBAC). A nurse shouldn’t be able to pull up records for patients on another floor, and a billing clerk definitely shouldn’t see clinical notes. Your code has to enforce this separation of duties.
Likewise, the requirement for “audit controls” isn’t just about having some basic logs. It means you need to create detailed, immutable audit trails that record every single interaction with ePHI. Who accessed it? When did they access it? What did they do? These logs aren’t just for debugging; they’re a legal requirement and the first thing auditors will ask for.
To get a handle on all these moving parts, a good HIPAA compliance checklist can be an invaluable tool for keeping your team on track.
Don’t Forget Your Business Associate Agreements
Your application will almost certainly rely on third-party services for cloud hosting with a provider like Amazon Web Services, analytics, or email notifications. If any of these vendors handle, store, or transmit ePHI on your behalf, HIPAA considers them a “Business Associate.”
This is a critical distinction. It means you are legally required to have a signed Business Associate Agreement (BAA) with every single one of them. A BAA is a contract that legally obligates your vendor to protect PHI with the same rigor that you do.
Pro Tip: Simply using a service like AWS or Google Cloud doesn’t automatically grant you HIPAA compliance. You have to sign a BAA with them and use only their specific HIPAA-eligible services. Even then, the ultimate responsibility for correctly configuring those services and securing the data falls squarely on you.
Skipping the BAA is one of the easiest and most expensive mistakes you can make. It leaves your organization wide open to massive liability because, under HIPAA, you are responsible for the compliance failures of your vendors. Getting this right is a foundational step you have to take before making any major architectural decisions.
Architecting Your Application for Rock-Solid Compliance
When you’re building a HIPAA-compliant application, security can’t be an afterthought; it has to be the blueprint. Your architecture is the foundation of your entire system. A single crack can compromise everything. This means every decision, from picking a cloud provider to designing your database schema, must be made through the lens of compliance.

The first major choice you’ll face is the cloud environment. Big players like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer HIPAA-eligible services and will sign a Business Associate Agreement (BAA). But here’s the catch: it’s a shared responsibility model. They handle the security of the cloud, but you are 100% responsible for securing what you put in the cloud.
This is where deep expertise in custom software development becomes critical. You need a team that knows precisely how to configure these powerful services to build a resilient and compliant application, a skill we’ve sharpened over many successful client cases.
A Defense-in-Depth Security Strategy
For any HIPAA-compliant build, the gold standard is a “defense-in-depth” approach. Think of your application like a medieval fortress. You don’t just have one tall wall; you have a moat, an outer wall, an inner wall, and guards at every gate. If one layer is breached, another is waiting to stop an attacker.
This strategy is all about layering independent security controls throughout your entire technology stack. It’s not enough to just have a firewall. You need network segmentation, application-level hardening, and strict data-level protections all working together.
-
Network Level Security: This starts with using Virtual Private Clouds (VPCs) to create totally isolated network environments. From there, you configure aggressive firewall rules and security groups to ensure only pre-approved, legitimate traffic ever reaches your servers.
-
Application Level Security: We’re talking about more than just a login screen. Implement robust user authentication with multi-factor authentication (MFA) as a default. Enforce strict, automatic session timeouts to prevent unauthorized access from a device that’s been left unattended.
-
Data Level Security: This is your last and most important line of defense. All PHI must be encrypted, access needs to be locked down, and every single interaction has to be logged. No exceptions.
By weaving these controls together, you create a system where a single point of failure is far less likely to turn into a catastrophic data breach. This philosophy is fundamental to modern healthcare software development.
Handling Data with End-to-End Encryption
Let’s be clear: encryption is non-negotiable. HIPAA demands that you protect PHI both when it’s moving across a network (“in transit”) and when it’s just sitting in a database (“at rest”).
For data in transit, the rule is Transport Layer Security (TLS) 1.2 or higher for all communications. This is what encrypts data as it travels between a user’s phone and your servers, preventing anyone from snooping on the connection.
For data at rest, the industry standard is AES-256 encryption. This applies to everything: your databases, your file storage (like AWS S3), and all of your backups. While most cloud providers have managed encryption services to help, it’s on you to ensure they are turned on and configured correctly.
Key Takeaway: End-to-end encryption isn’t a feature; it’s a foundational requirement. Failing to encrypt PHI at every stage is one of the most common and most easily avoidable HIPAA violations we see.
Robust Audit Logging and Access Controls
If you can’t prove who did what and when, you can’t prove compliance. Comprehensive audit logging is a core technical safeguard under HIPAA, and it’s something auditors will check for immediately. Your application must generate detailed, immutable logs for any event that touches PHI.
This means you need to be recording:
-
Every login attempt, both successful and failed.
-
Every time a user views, creates, updates, or deletes PHI.
-
Any change to user permissions or other security settings.
-
All administrative actions performed on servers or databases.
These logs have to be stored securely and protected from being altered. They are your first line of defense for spotting suspicious activity and are absolutely essential during a security incident investigation.
Working hand-in-hand with logging is fine-grained access control. Your guiding philosophy here must be the “Principle of Least Privilege.” Simply put, users should only have access to the absolute minimum amount of data needed to do their jobs. Role-Based Access Control (RBAC) is the standard way to enforce this, tying a user’s permissions directly to their role in the organization.
Building these systems requires meticulous planning and real-world technical experience. As a leading AI solutions partner, we help organizations design and implement these crucial architectural components, ensuring their applications are secure, scalable, and compliant right from the start.
Weaving AI and Machine Learning into Your HIPAA Strategy
Artificial intelligence is making huge waves in healthcare, from predicting disease outbreaks to crafting personalized treatment plans. But let’s be honest: when you bring AI and machine learning into an app that touches Protected Health Information (PHI), you’re also inviting a whole new level of compliance headaches. Building a HIPAA-compliant app today means you have to be just as obsessed with patient privacy as you are with innovation.
This isn’t just a hypothetical concern. The mobile health market is on a rocket ship trajectory, expected to blast past $300 billion by 2026. What’s fueling that growth? AI-powered symptom checkers and remote monitoring tools that absolutely must be HIPAA compliant. This push for smarter, connected care also puts a giant target on these apps.
The only way to navigate this is to adopt a security-first mindset right from the start of your AI development lifecycle. It can’t be an afterthought.
Keeping PHI Out of Your Machine Learning Models
Here’s the fundamental challenge: machine learning models are data-hungry. In healthcare, that data is some of the most sensitive information imaginable. You simply cannot dump raw patient records into a training algorithm. That’s not just a bad idea; it’s a direct HIPAA violation that could lead to your model memorizing and spitting out someone’s personal details.
To avoid that nightmare scenario, you need a rock-solid plan for handling data before it gets anywhere near your model.
-
Anonymize and De-identify Everything: This is your first line of defense. Before you even think about training, you have to meticulously scrub all 18 HIPAA identifiers: things like names, birthdays, and zip codes, from your dataset. And this can’t be a one-way street; the process needs to be irreversible to be truly effective.
-
Consider Synthetic Data: Sometimes, the safest play is to create an entirely artificial dataset that’s statistically identical to the real thing. Synthetic data mimics the patterns and relationships found in real PHI without containing a single shred of actual patient information. It’s a powerful, compliant way to get your models trained up.
These techniques train your models to recognize clinical patterns, not personal identities. That’s the key.
Building a HIPAA-compliant AI model has less to do with the specific algorithm you pick and more to do with the integrity of the data pipeline you build around it. Your absolute focus has to be on protecting that source data at every single step.
Locking Down Large Language Models
Large language models (LLMs), the brains behind advanced chatbots and clinical note summarizers, come with their own special set of risks. A carelessly implemented LLM can become a PHI-leaking machine. A user might paste sensitive info into a prompt, or the model could accidentally surface details from its training data in a response.
You have to implement strict protocols here. A really effective architecture I’ve seen work well is a secure proxy that acts as a gatekeeper between your application and the LLM provider, like OpenAI or Anthropic.
This proxy is designed to intercept every request, scan for and strip out any PHI before it leaves your secure environment, and then filter the model’s response on the way back to catch any potential leaks.
This “secure proxy” pattern is a core part of our own AI development services because it lets healthcare organizations tap into the power of AI for your business without gambling on compliance. For more on the principles that guide this approach, you should read our guide on responsible AI.
A Real-World Example: AI-Powered Diagnostics
Let’s make this tangible. Imagine you’re building an AI tool that analyzes medical images to spot the early signs of a disease. Here’s how you’d build it the right way:
-
Secure Ingestion: First, the images and patient notes (all PHI) land in a secure, HIPAA-compliant cloud environment. Think of it as a digital vault.
-
De-identification Pipeline: An automated workflow immediately kicks in. It strips all identifiers from the notes and image metadata, swapping them with a unique, randomized ID. The original, identifiable PHI is firewalled off in a separate, highly restricted database.
-
Isolated Model Training: Now, the fully anonymized dataset is moved to a secure, isolated training environment, like a HIPAA-configured instance of AWS SageMaker or Azure Machine Learning. The model trains here, completely blind to patient identities.
-
Inference with Anonymized Data: When a doctor uploads a new image for analysis, it goes through that exact same de-identification pipeline. Only the clean, anonymized data is sent to the trained AI model for its analysis.
-
Secure Re-association: The model’s output, the diagnosis, is sent back to the application’s secure backend. Only there is it re-associated with the original patient ID and presented securely to the authorized clinician.
This flow lets you use the incredible power of AI without ever putting raw PHI on the line. It’s the perfect marriage of cutting-edge innovation and airtight security.
Weave Security into Your Development Lifecycle
Thinking about HIPAA compliance as a final checkbox before launch is a recipe for disaster. Real security, the kind that stands up to audits and actual threats, has to be baked into your software development lifecycle (SDLC) from day one. This is what we mean by a “Shift Left” approach: tackling security concerns at the design stage, not patching them after the fact.
The healthcare app market is absolutely exploding, with projections showing it could hit $4,710.54 billion by 2034. With that kind of growth, robust, HIPAA-compliant practices are no longer optional. They’re table stakes. Adding to the pressure, the HHS’s 2025 HIPAA Security Rule update is expected to do away with ‘addressable’ specifications. That means all cybersecurity measures, from advanced encryption to strict risk assessments, are about to become mandatory.
Here’s a look at how data should flow in a compliant AI application, where PHI is carefully handled to protect patient privacy.
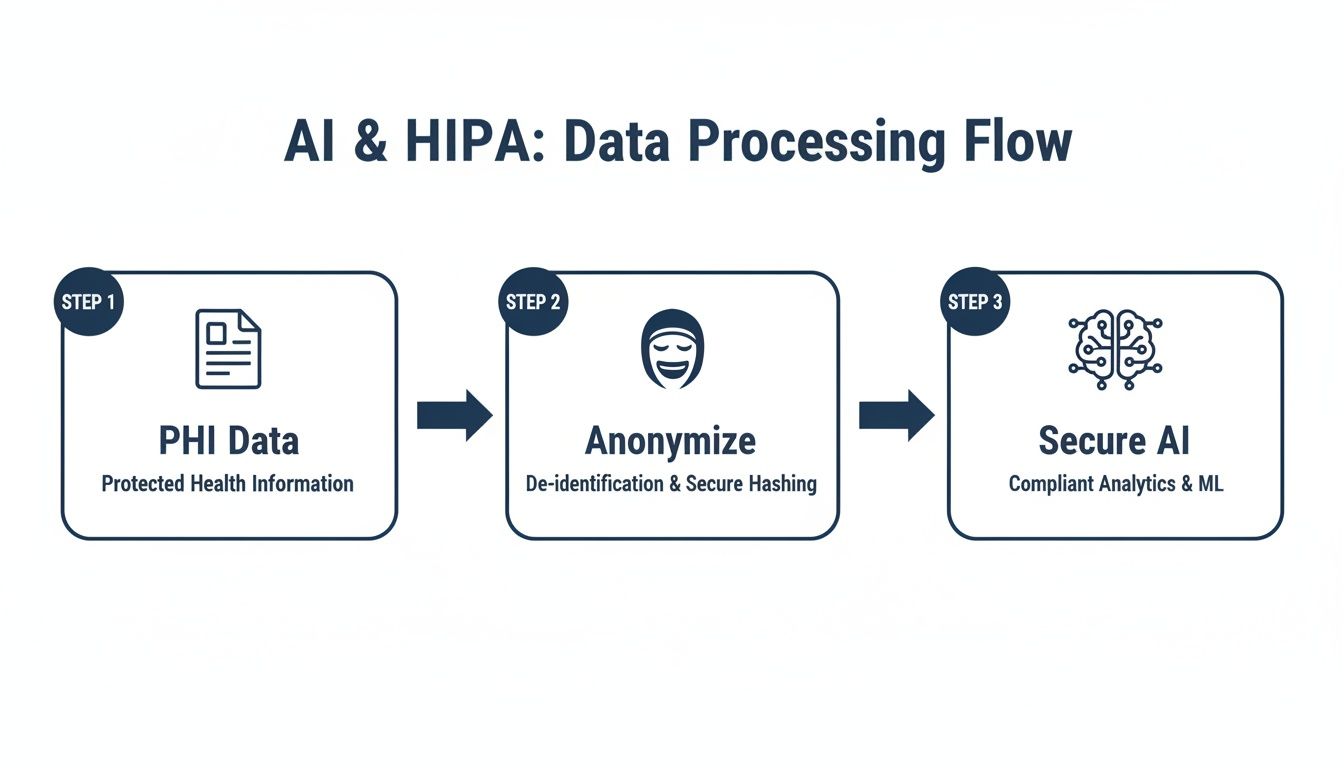
The critical takeaway here is that Protected Health Information (PHI) is stripped of its identifiers before it ever gets near an AI model. This de-identification process is fundamental, ensuring the model learns from clinical data, not someone’s personal information.
Automating Security in Your CI/CD Pipeline
Your CI/CD (Continuous Integration/Continuous Delivery) pipeline is your best friend for automating security. By building security checks directly into your development workflow, you can catch vulnerabilities early on, which is always cheaper and easier than fixing them in a live environment.
This isn’t just about efficiency; it’s about making compliance a repeatable, reliable part of your process instead of a manual, error-prone headache. Every single code commit gets scrutinized before it can ever be deployed.
Here are the essential automated checks you should have in your pipeline:
-
Static Application Security Testing (SAST): Think of these tools as a spell-checker for security flaws. They scan your source code for common vulnerabilities like SQL injection or weak error handling before the code is even compiled.
-
Dynamic Application Security Testing (DAST): DAST tools are more like a penetration tester in a box. They attack your running application to find vulnerabilities that only show up when the code is actually executing.
-
Software Composition Analysis (SCA): Let’s be honest, modern apps are mostly assembled from open-source libraries. SCA tools are indispensable for scanning these third-party dependencies for known vulnerabilities, so a flaw in someone else’s code doesn’t become your breach.
By embedding these scans, you create a powerful security gate. Vulnerable code simply doesn’t get to pass. As we explored in our guide to building a secure software development lifecycle, these practices are essential for robust security.
Vigilance After Launch: Monitoring and Incident Response
Getting your application live is just the beginning. HIPAA mandates continuous monitoring to spot and respond to security incidents in real time. This is more than just glancing at server logs; it’s an active hunt for anything that looks out of place.
A solid monitoring strategy includes:
-
Centralized Logging: Pull logs from everything: your apps, servers, firewalls, you name it, into a single, searchable system. This gives you a bird’s-eye view to connect the dots and spot suspicious activity across your entire infrastructure.
-
Smart Alerting: You can’t watch logs 24/7. Set up automated alerts for specific events that scream “trouble,” like repeated failed logins from one IP address or a sudden attempt to export thousands of patient records.
-
Ongoing Vulnerability Scanning: Just because you scanned in development doesn’t mean you’re done. Your live environment needs regular, automated vulnerability scans to catch new threats as they are discovered.
A Word of Experience: Your Incident Response Plan is just as critical as all your firewalls and encryption. Don’t just write one, test it. When a breach happens (and you should always operate as if it’s a matter of when, not if), your team needs a clear, practiced playbook to contain the damage and meet HIPAA’s strict breach notification deadlines.
The Rhythm of Risk Assessments
Finally, HIPAA requires you to conduct formal risk assessments on a regular basis. This is where you methodically identify potential threats to PHI, figure out how likely they are to happen and what the impact would be, and then put controls in place to manage those risks.
This isn’t a one-and-done audit you can file away. It’s a living document. Any time you introduce a major feature, integrate with a new vendor, or make a significant architectural change, it’s time for another risk assessment. It’s this constant, proactive posture that keeps your application compliant as your product and the threat landscape evolve.
Frequently Asked Questions
What actually makes an application HIPAA-compliant?
A truly HIPAA-compliant application integrates administrative, physical, and technical safeguards. Key technical requirements include end-to-end encryption for data both at rest and in transit, strict role-based access controls (RBAC) to enforce the principle of least privilege, and comprehensive, immutable audit logs to track all interactions with Protected Health Information (PHI). Additionally, you must have a signed Business Associate Agreement (BAA) with all third-party vendors who handle PHI.
Can I use a standard cloud provider like AWS or Azure?
Yes, but you must operate under their “shared responsibility model.” Providers like AWS, Azure, and Google Cloud offer HIPAA-eligible services and will sign a BAA. They are responsible for the security of the cloud (physical data centers, core infrastructure), but you are 100% responsible for the security in the cloud. This includes correctly configuring services, securing your application code, and managing all data you store on their platform.
What are the biggest mistakes to avoid in development?
The most common errors include failing to encrypt PHI everywhere (both at rest and in transit), implementing weak or overly permissive access controls, and neglecting to create detailed audit trails. Another major pitfall is not obtaining a signed BAA from every vendor that touches PHI. The single biggest strategic mistake, however, is treating compliance as a last-minute checklist instead of integrating it into the entire software development lifecycle from the very beginning.
How does HIPAA apply to mobile health apps?
If a mobile app creates, receives, maintains, or transmits electronic PHI on behalf of a covered entity, it must be fully HIPAA-compliant. This means any data stored locally on the device must be encrypted, all communication between the app and the backend must use strong TLS encryption, and the backend infrastructure itself must adhere to all HIPAA security rules. Special attention must also be paid to secure user authentication and ensure that sensitive information is never exposed in push notifications.
At Bridge Global, we specialize in turning complex compliance challenges into secure, scalable, and successful digital health solutions. As your trusted AI solutions partner, we build applications that protect patient data and drive innovation.



